Netflix Clone – DevSecOps CI/CD with Monitoring
Overview
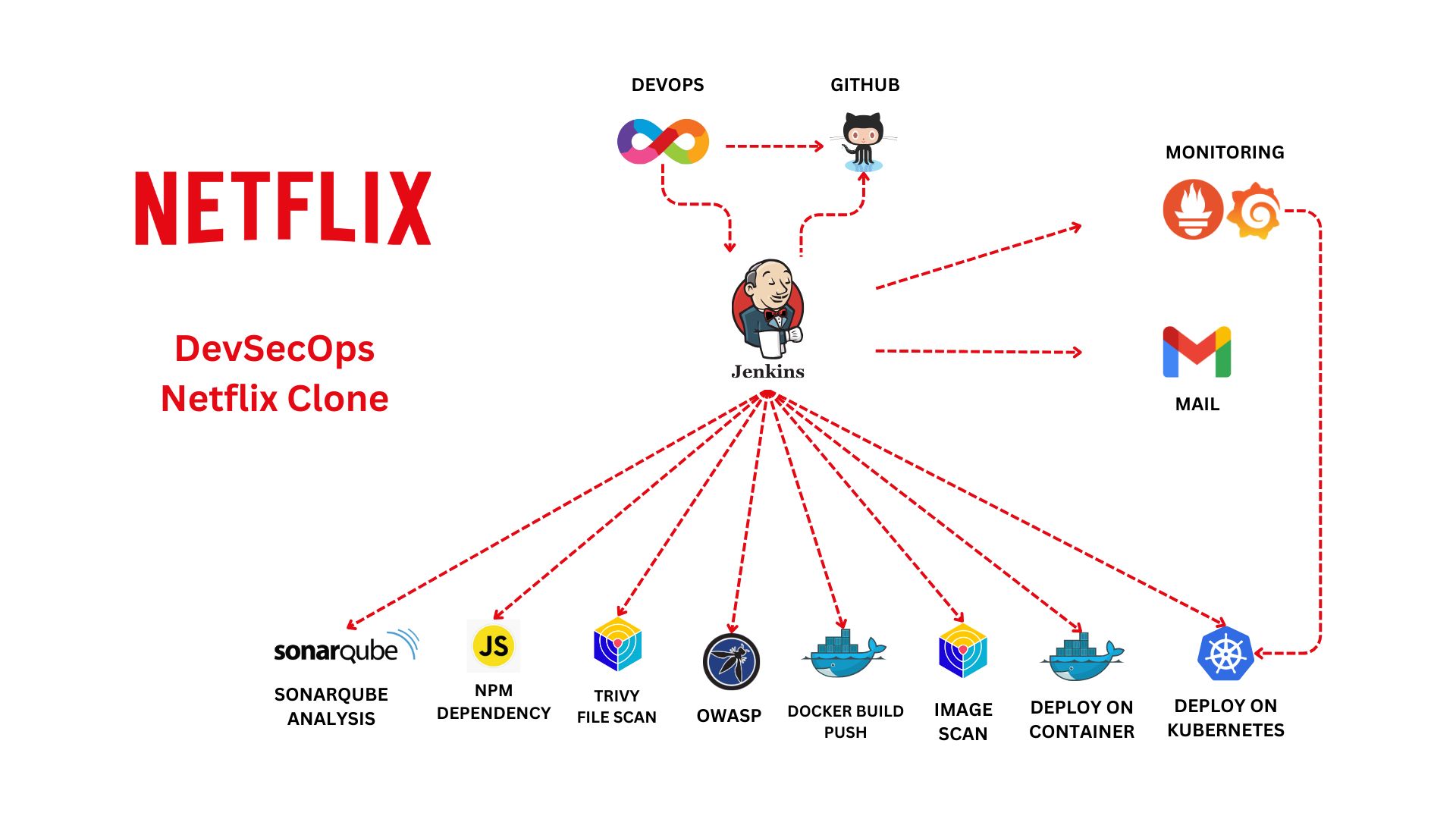
This project demonstrates a real-world DevSecOps pipeline by deploying a Netflix Clone application using modern cloud-native tools.
It integrates CI/CD automation, security scanning, containerization, Kubernetes orchestration, and monitoring—all running on AWS infrastructure.
The goal was to simulate how production-grade applications are built, secured, deployed, and observed in real environments.
Project Objectives
- Automate build, test, and deployment using Jenkins
- Integrate security checks into the CI/CD pipeline (DevSecOps)
- Deploy containerized applications using Docker and Kubernetes
- Monitor infrastructure and application metrics in real time
- Implement alerting and email notifications for pipeline events
Architecture Highlights
- Jenkins-based CI/CD pipeline
- Docker for containerization
- Kubernetes cluster for orchestration
- SonarQube, Trivy, OWASP Dependency Check for security
- Prometheus + Grafana for monitoring and observability
- AWS EC2 as the cloud infrastructure
Key Features
⚙️ Automated CI/CD pipeline using Jenkins
🔐 Security scanning at multiple stages:
- Static Code Analysis (SonarQube)
- Container Vulnerability Scanning (Trivy)
- Dependency Vulnerability Checks (OWASP Dependency Check)
📦 Docker image build and push
☸️ Kubernetes deployment with master–worker setup
📊 Monitoring Jenkins & Kubernetes metrics
📈 Dashboards with Prometheus and Grafana
📧 Email notifications integrated with Jenkins
Tech Stack
- CI/CD: Jenkins (Declarative Pipeline)
- Containerization: Docker
- Orchestration: Kubernetes
- Security: SonarQube, Trivy, OWASP Dependency Check
- Monitoring: Prometheus, Grafana, Node Exporter
- Cloud: AWS EC2 (Ubuntu 20.04 / 22.04)
- API: TMDB API
Project Workflow
- Launch AWS EC2 instances (Ubuntu 22.04 & 20.04)
- Install Jenkins, Docker, Trivy
- Run SonarQube as a Docker container
- Generate TMDB API key for the Netflix clone
- Install Prometheus and Grafana on monitoring server
- Integrate Prometheus with Jenkins
- Configure Jenkins email notifications
- Install required Jenkins plugins:
- JDK
- SonarQube Scanner
- NodeJS
- OWASP Dependency Check
- Create a Jenkins Declarative Pipeline
- Perform security scans during pipeline execution
- Build and push Docker images
- Deploy the application using Docker
- Set up Kubernetes master and worker nodes
- Deploy the Netflix Clone on Kubernetes
- Access the application via browser
- Clean up resources by terminating EC2 instances
Monitoring & Observability
- Jenkins metrics tracked via Prometheus
- Node-level metrics using Node Exporter
- Kubernetes cluster monitoring
- Grafana dashboards for real-time visualization
What This Project Demonstrates
- Strong understanding of DevSecOps principles
- Hands-on experience with production-like CI/CD pipelines
- Security-first approach in application delivery
- Cloud-native deployment using Kubernetes
- Observability and monitoring best practices
Use Cases
- DevSecOps learning and demonstrations
- CI/CD pipeline reference project
- Kubernetes + monitoring practice
- Resume and portfolio showcase for DevOps roles
Future Improvements
- Helm-based Kubernetes deployments
- Horizontal Pod Autoscaling (HPA)
- Centralized logging with Loki or ELK
- Slack / Teams notifications
- GitOps-based deployment with Argo CD
Screen Shot Images
License
MIT License © 2025
Built to showcase real-world DevSecOps practices, not just theory 🚀
By Omprakash Chauhan